User Access Policies are a feature in Salesforce that provides a flexible and centralized way to manage user access and permissions across the organization. This feature allows administrators to define and enforce access controls based on various criteria, ensuring that users have appropriate permissions according to their roles, departments, and specific use cases. User access policies, now generally available, include some enhancements since the Spring ’24 release. You can now create 200 active policies, up from 20, and set the order in which active policies are run.
How: From Setup, in the Quick Find box, enter User Management Settings, and then select User Management Settings. Turn on User Access Policies.
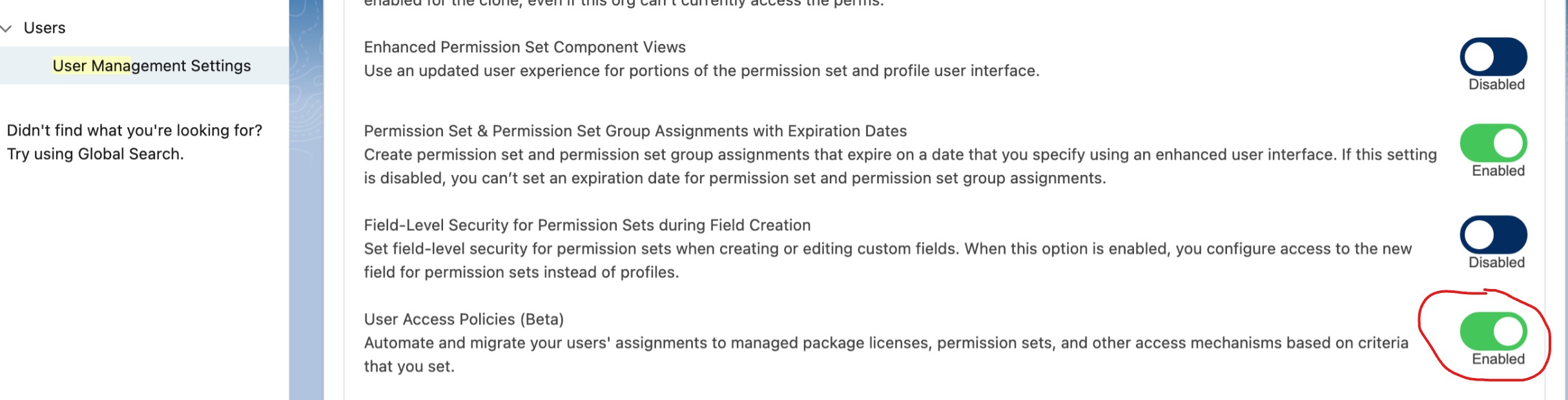
To create or manage your user access policies, in the Quick Find box, enter User Access Policies, and then select User Access Policies.
Now set up a user access policy
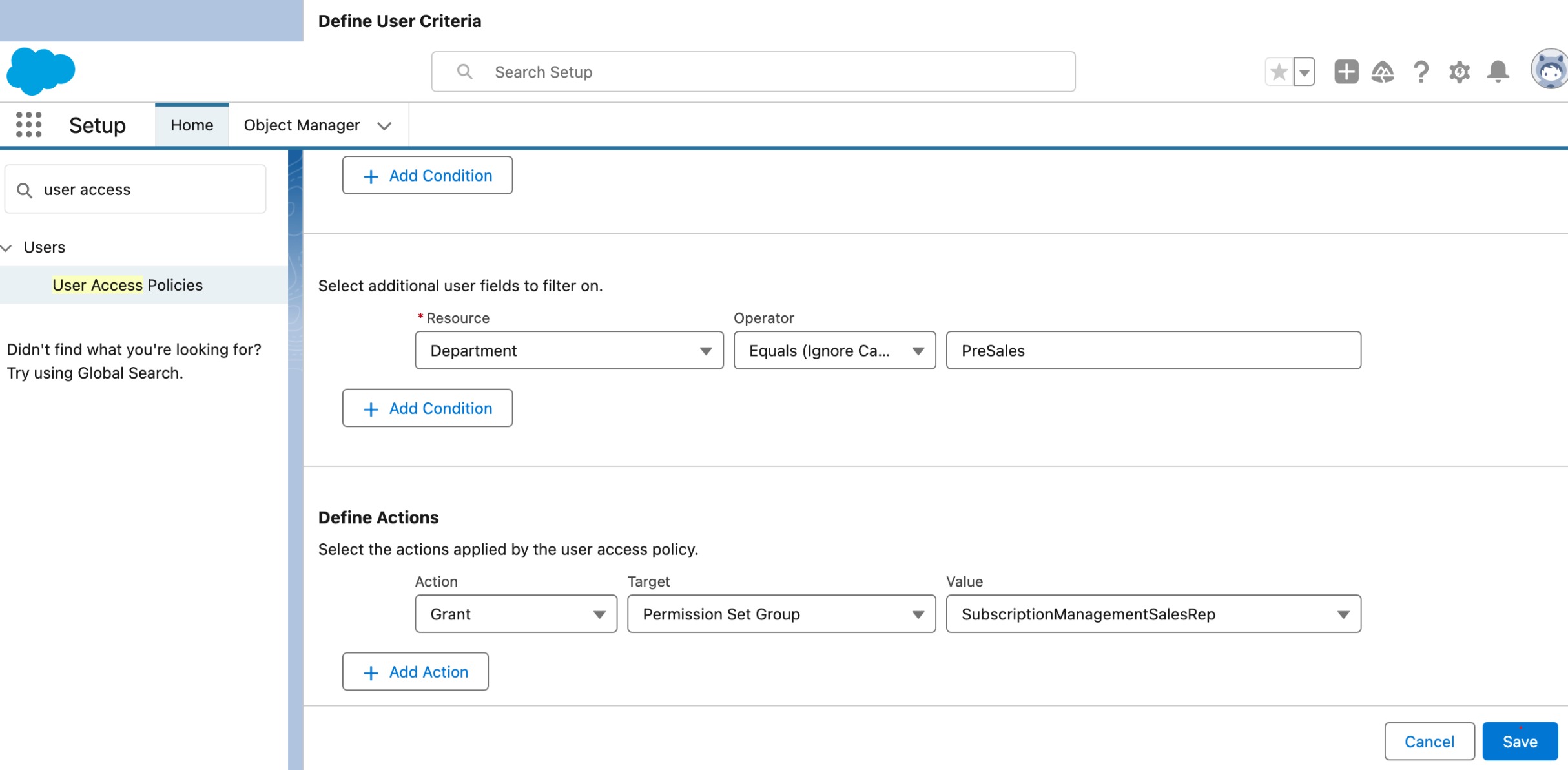
Key Features and Components
- Policy-Based Access Control (PBAC):
- Granularity: Policies can be defined with fine-grained rules, allowing for precise control over which users can access specific resources.
- Contextual Access: Policies can take into account the context in which access is requested, such as the user’s location, device, or time of day.
- Centralized Management:
- Unified Interface: Administrators can create, manage, and review policies from a centralized interface, making it easier to maintain and audit access controls.
- Automation: Policies can be automated to dynamically adjust permissions based on changing conditions or criteria.
- Dynamic Evaluation:
- Real-Time Enforcement: Access policies are evaluated in real-time, ensuring that changes in user status or context are immediately reflected in their access permissions.
- Condition-Based Rules: Policies can include conditions that must be met for access to be granted, such as specific attributes of the user or the resource being accessed.
- Customizable Rules:
- Attribute-Based Access Control (ABAC): Policies can use user attributes (e.g., department, role, seniority) and resource attributes to determine access.
- Role Hierarchies and Constraints: Policies can respect organizational role hierarchies and enforce constraints accordingly.
Use Cases for User Access Policy
- Role-Based Access Control (RBAC):
- Scenario: A company wants to ensure that only sales managers can approve discounts on deals.
- Solution: Create profiles and permission sets that grant the necessary permissions to sales managers and restrict access for other roles. Use the role hierarchy to ensure managers can access their subordinates’ data.
- Temporary Access for Projects:
- Scenario: A user needs temporary access to a new feature for a special project.
- Solution: Assign a permission set with the required permissions for the duration of the project and remove it once the project is completed.
- Regulatory Compliance:
- Scenario: A financial institution needs to ensure that only authorized personnel can access sensitive customer data.
- Solution: Use profiles to enforce strict access controls and permission sets to grant specific permissions as needed. Apply sharing rules to restrict data access based on regulatory requirements.
- Segregation of Duties:
- Scenario: A company wants to ensure that users who create purchase orders cannot approve them.
- Solution: Create separate profiles for users who create and approve purchase orders. Use permission sets to grant specific permissions as necessary and implement sharing rules to enforce segregation of duties.
- Field-Level Security:
- Scenario: Sensitive information such as Social Security numbers needs to be hidden from most users.
- Solution: Use field-level security settings within profiles to restrict access to sensitive fields, ensuring that only authorized users can view or edit them.
- Managing Large User Groups:
- Scenario: An organization with a large sales team needs to efficiently manage permissions for different regions.
- Solution: Create permission set groups for each region, containing all necessary permissions. Assign these groups to users based on their region, simplifying permission management.
- Data Sharing in Collaborative Environments:
- Scenario: A team of users from different departments needs to collaborate on shared projects.
- Solution: Use sharing rules to grant access to project-related data across departmental boundaries while maintaining overall data security.
Differences from Profiles and Permission Sets
- Profiles:
- Static Assignment: Profiles are assigned to users and define a baseline set of permissions that do not change dynamically based on context or conditions.
- Role-Based: Profiles are generally role-based, meaning they are designed to fit users within predefined roles within the organization.
- Permission Sets:
- Supplementary: Permission sets extend user permissions beyond what is granted by their profile, allowing for more granular access control.
- Manual Assignment: Permission sets are manually assigned to users and do not dynamically adjust based on context or conditions.
- User Access Policies:
- Dynamic and Contextual: Unlike profiles and permission sets, user access policies can dynamically adjust permissions based on real-time conditions and user attributes.
- Centralized and Automated: User access policies offer a centralized and automated way to manage and enforce access rules, reducing the need for manual intervention and making it easier to adapt to changes in the organization.
Example Scenario
Consider a financial services company that needs to ensure compliance with strict data access regulations. The company can define user access policies to restrict access to sensitive customer data based on user roles, locations, and devices. For instance, a policy might allow access to customer financial data only if the user is a financial analyst, accessing the system from a secure office location, and during business hours.
In this scenario, traditional profiles and permission sets might not provide the necessary flexibility and granularity, as they cannot enforce such dynamic conditions. User access policies fill this gap by allowing the company to define and enforce complex access rules that adapt to real-time conditions.
In summary, User Access Policies in Salesforce offer a sophisticated and flexible approach to managing user access, providing dynamic, context-aware controls that go beyond the capabilities of traditional profiles and permission sets. This feature is particularly valuable for organizations with complex access requirements and stringent security or regulatory compliance needs.